Site blog
In an increasingly digital world, understanding the nuances of online safety is paramount. One of the most prevalent threats today is phishing scams, where individuals are tricked into divulging sensitive information under the guise of legitimate communication. The Federal Trade Commission (FTC) has taken a significant step forward in educating young people about these dangers through the launch of its game, "OnGuard Online." This interactive tool not only raises awareness but also provides practical strategies to identify and combat phishing attempts effectively.
The FTC's OnGuard Online initiative is anchored in its commitment to promote cybersecurity among youth, as they are often prime targets for cybercriminals. With the gamification of learning, the program transforms traditional educational methods into engaging experiences. This is particularly vital in a landscape where young individuals are typically more tech-savvy but may not possess adequate knowledge of online threats.
The game's design is rooted in real-life scenarios that teenagers may encounter, making it relatable and immediately applicable. Players navigate various challenges that mimic the tactics used by phishing scammers. For instance, they are presented with messages that could come from social media platforms, their favorite gaming sites, or even email correspondence. As they progress through the game, players learn to discern red flags and indicators of phishing, such as suspicious links or requests for personal information.
One remarkable feature of the OnGuard Online game is its interactive feedback mechanism. After each scenario, players receive instant feedback on their decisions, which not only reinforces learning outcomes but also encourages critical thinking. This approach is particularly effective for younger audiences, as it allows them to grasp complex concepts in a straightforward and enjoyable manner. By failing a scenario, players can understand the consequences of their mistakes, leading to a deeper comprehension of phishing tactics.
Moreover, the FTC's game does not simply stop at teaching about phishing; it encompasses other vital aspects of online safety that are crucial for young individuals. Topics such as password management, safe social media practices, and the importance of privacy settings are integrated into the gameplay. This holistic approach ensures that players are not just equipped to handle phishing scams but are also empowered to navigate the wider sphere of online risks.
The success of the OnGuard Online game can be attributed significantly to its accessibility. Young users can engage with it from any device, whether it be smartphones, tablets, or computers—an essential factor given the diverse modes of internet access that youth utilize. In an age where gaming is a universal attraction, the OnGuard Online initiative finds itself at the intersection of education and entertainment, making it easier for teenagers to engage with important material that directly impacts their safety.
Furthermore, the initiative serves as a vital resource for educators and parents. By incorporating the game into educational curricula or discussing it at home, they can foster a proactive approach to online safety. The FTC has also provided supplementary materials and GOOGLE DELETE PHISING resources for adults to help facilitate discussions regarding digital literacy and security, ensuring that the message of online safety permeates into the home and educational environments.
The OnGuard Online game aligns with contemporary educational trends that prioritize experiential learning. As traditional classroom settings often shy away from addressing the pressing issues of cybersecurity, this game fills a significant gap. It allows students to learn in a dynamic context, simulating real-life applications that have immediate relevance to their daily lives. This innovative methodology supports the notion that learning is not merely confined to textbooks but can thrive through interactive and engaging experiences.
As we move further into the digital age, the necessity for resources such as OnGuard Online will only grow. The use of technology to enhance learning about cybersecurity, particularly in relation to phishing scams, represents a commendable advance in fostering digital literacy among younger populations. The FTC's initiative not only empowers youth to defend themselves against potential scams but also ignites discussions and awareness around broader cybersecurity issues.
In conclusion, FTC's OnGuard Online game signifies a pivotal advancement in the fight against phishing scams, particularly for youth. Its engaging, interactive format, combined with real-world application, equips young individuals with the knowledge and skills necessary to protect themselves online. With a commitment to expanding digital literacy, the FTC offers a proactive solution to a pervasive problem, ensuring that the next generation is more prepared to handle the challenges of an ever-evolving digital landscape. By fostering an environment where young people can learn about online threats through play, the OnGuard Online initiative stands as a model for future efforts in cybersecurity education.
The digital landscape is often fraught with threats, with cybersecurity companies like Avast at the forefront of protecting users from online scams. In a recent incident that has garnered widespread attention, Avast's online security software erroneously classified a legitimate website as a phishing threat, sending ripples through its user community. This mix-up has raised questions about the reliability of automated cybersecurity tools, their impact on businesses, and the rights of users navigating the internet.
In a recent incident that has garnered widespread attention, Avast's online security software erroneously classified a legitimate website as a phishing threat, sending ripples through its user community. This mix-up has raised questions about the reliability of automated cybersecurity tools, their impact on businesses, and the rights of users navigating the internet.
The incident occurred on April 15, when users reported that Avast had blocked access to the website belonging to Legit Web, a popular platform known for its user-friendly interface and commitment to customer service. Upon trying to access the site, users were met with a stark warning from Avast, which stated that the page was a potential phishing site designed to steal personal information. This alarmed many, particularly small business owners and freelancers who relied heavily on the platform for their operations.
Following the block, a wave of complaints flooded social media as users expressed outrage. Many users stated that they felt disheartened and frustrated by the incident, emphasizing the potential loss of revenue and GOOGLE DELETE PHISING trust in Legit Web. "Our whole business runs on that platform, and now we have to look for alternatives," shared Maria Lopez, a graphic designer whose clientele is largely based on projects from Legit Web. "It’s not just an inconvenience; it’s detrimental to our livelihood."
In response to the rising uproar, Avast released a statement acknowledging the error. The company explained that its automated security systems rely on databases and algorithms to evaluate the safety of websites. Unfortunately, the algorithm had mistakenly flagged Legit Web due to a combination of factors, including recent changes to its URL structure and an uptick in negative reports that, upon analysis, were unfounded. The statement reassured users that the incident was being investigated and that efforts were underway to prevent such occurrences in the future.
Phishing attacks continue to be a significant concern in the cybersecurity field, with hackers constantly devising new tactics to lure unsuspecting individuals into revealing sensitive information. Consequently, security software is critical in providing users with warnings about potentially dangerous sites. However, this reliance on automated systems has a flip side, as seen in this scenario where a legitimate website is misidentified as a threat.
Experts in the field suggest that such incidents bring to light the challenges inherent in automated flagging systems. "While automated systems can process vast amounts of data quickly, there's always a margin of error," stated Dr. Michael Roberts, a cybersecurity analyst. "When these systems are mistaken, the fallout can be significant, especially for businesses that depend on their online presence. It underscores the need for a hybrid system where automated tools are supported by human oversight."
The unintended consequences of this misclassification extended beyond individual users. Legit Web's representatives reported a substantial increase in customer service inquiries, as many users were panicked by the warning and sought clarification on whether their data had been compromised. The site’s creators swiftly initiated communication with Avast to resolve the issue and ensure that users were informed about the real situation.
Online businesses thrive on trust, and an automated phishing flag can damage that trust quickly. Some business owners expressed concerns that their reputation might suffer irreparable harm due to this incident. "We’ve spent years building our brand and reputation, and now we risk losing that due to a software blunder," said Tom Harris, the CEO of Legit Web. "We hope Avast rectifies this issue quickly and reinstates our site to avoid more unnecessary damage."
In the wake of the incident, it has become increasingly essential for users to remain vigilant, understanding that while cybersecurity tools are designed to protect them, they are not infallible. VPNs, firewalls, and antivirus software provide layers of security, but the onus is also on individuals and businesses to verify the legitimacy of sites before inputting sensitive information.
Cybersecurity companies must take these missteps seriously and work towards systems that reduce the chances of wrongful blocks in the future. As Avast works to rectify the situation and the dust settles, users are left navigating the complexities of online threats with a newfound understanding: the fight against cybersecurity risks is a continuous battle filled with uncertainties, even from those entrusted to safeguard us.
As the story develops, users and businesses alike will be watching closely how Avast handles its response and what measures it adopts to reassure its community that they are safe in their online endeavors.
Türkiye’deki escortlar, kültürlü ve eğitimli insanlardır. Onlar, müşterilerine sadece fiziksel hizmetler sunmakla kalmaz, aynı zamanda onlarla kaliteli zaman geçirir ve sohbet ederler. Türkiye’deki escortlar, müşterilerine unutulmaz anılar yaşatmak için her türlü hizmeti sunarlar. Aradığınızı muhakkak bulacaksınız. ataşehir escort vip hizmeti veriyor. Türkiye’deki escortlar, müşterilerine çeşitli hizmetler sunarlar. Eşlik Hizmeti almak için, Akdeniz bölgesinde antalya escort sitesi sizler için idealdir.. Müşterilerine eşlik ederek onların yalnız geçireceği zamanları daha keyifli hale getirirler. Masaj Hizmeti almak için, bodrum escort sayfası online yayında. Müşterilerine rahatlatıcı ve keyifli bir masaj hizmeti sunarlar. Müşterilerinin isteklerine göre özel hizmetler sunarlar. Bu hizmetler, müşterinin tercihine bağlı olarak değişiklik gösterebilir. Sonuç olarak taksim escort kadınları da tümü kadar ünlüdür. Onlar, müşterilerine unutulmaz anılar yaşatmak için her türlü hizmeti sunarlar. Türkiye’deki escortlarla geçirilen zaman, hem keyifli hem de unutulmaz olacaktır. Sence ben güzel bir kadın mıyım? Kayseri escort bayan ilanımdaki resimler karar vermen konusunda eğer sana yardımcı olmazsa o zaman hiç çekinmeden ara beni bebeğim, ben sana burada bile olmayan resimlerimi gönderebilirim.
Sitemizin bu bölümünde siz değerli diyarbakırlılar için; Diyarbakır’da erkek arayan dul bayanlar, Diyarbakır’da erkek arayan zengin bayanlar, Diyarbakır’da erkek arayan olgun kadınlar Birgül Diyarbakır’da erkek arayan 55-60 yaş üstü bayanlar, Diyarbakır’da erkek arayan türbanlı ve tesettürlü kapalı bayanlar konularına değinmek ve sizleri bu konuda aydınlatmak, ve sizler için gerçekten hayatınızı renklendirecek insanı bulmanızı sağlayacak bir içerik oluşturmak istedim. Diyarbakır’da erkek arkadaş arayan bayanların büyük bir bölümü dul kadınlardan oluşuyor arkadaşlar. Çünkü günümüzde biliyorsunuz ki evlilikler çok kısa sürede bitiyor. Ülkenin büyük bir nüfusu artık dul kalmış durumda. Dul kadınlar Erkek arkadaş bulmak için sitemizi yoğun bir şekilde ziyaret ediyorlar. Özellikle de Diyarbakır şehrimizden sitemizi ziyaret eden dul kadınların Evlilik amaçlı ya da sevgili bulabilmek için ücretsiz olarak verdikleri ilanları kontrol etmenizi tavsiye ederim. Diyarbakır’da erkek arayan dul bayanların cep telefonu ve WhatsApp sohbet numaralarını ya da Facebook Twitter ve Instagram adreslerini kendilerinden isteyebilirsiniz. Bunun haricinde sitemiz üzerinde dul kadınların cep numaralarını paylaşmıyoruz.
Kızlık zarı genetik etkilerle de kişiden kişiye değişiklik gösterir. Özellikle ara bölmeli kızlık zarı yapısına sahip olan kişilerde cinsel ilişkiye girmede sorunlar oluşabilir. Kızlık zarının zarar görüp görmediği jinekologlar tarafından ufak bir muayene ile anlaşılabilmektedir ve bu muayene ağrısızdır. Kızlık zarının zarar görmesi kimi zaman kanama ile kim zaman da kırmızı bir akıntı ile kendisini gösterebilir. Kızlık zarının esnek olduğu durumlarda ilk ilişki sırasında kanama meydana gelmeyebilir. Kızlık zarının basit bir cerrahi ile onarılmasına hymenoplasti (himenoplasti) denmektedir. Kızlık Zarı Neden Vardır? Genellikle kızlık zarının bir işlevi olmadığı düşünülse de bazı bilim adamları tarafından kızlık zarının bazı işlevleri olduğu düşünülmektedir. Buna göre 11-12 yaşlarına kadar olan dönem içerisinde vajina içine mikropların girmesinin önlenmesi ilk işlevidir. İkinci işlevi ise doğuştan idrar kanalı yokluğu halinde çıkartılıp kullanılarak idrar kanalı yapılmasıdır. Kızlık Zarı Türleri Nelerdir? En çok rastlanan kızlık zarı türüdür. Genç kızların neredeyse %80′ninde bu türe rastlamak mümkündür. Annüler kızlık zarının yapısı yuvarlaktır.
Birlikte geçirdiğimiz zamanı unutulmaz kılmak için elimden geleni yapacağım. Hayatın monotonluğundan kaçmak ve birlikte tutkulu zaman geçirmek istiyorsanız, benimle iletişime geçin. Size özel bir deneyim yaşatmak için sabırsızlanıyorum, sizi bekliyorum. Diyarbakır Escort Bölgeleri en iyi hizmeti vermek için buradayım. Sizi mutlu ve memnun etmek benim tutkum haline geldi. Kendiniz için özel bir zaman geçirmek ve stresinizi unutmak istiyorsanız lütfen benimle iletişime geçin. İsterseniz randevu alabilir ya da beni arayabilirsiniz. Diyarbakır escort Duygu olarak sizlere verdiğim hizmetin her zaman özel ve kişisel olduğunu hatırlatmak isterim. Her randevu benim için bir macera, bir keşif yolculuğu. Sizinle geçirdiğim her anı özel kılmak ve unutulmaz anılar yaratmak için buradayım. İsteklerinizi dinlemek ve sizi memnun etmek için elimden geleni yapacağım. İster bir fanteziyi gerçekleştirmek, ister yeni bir şey deneyimlemek veya sadece rahatlamak isteyin, bana güvenebilirsiniz. Size doğru deneyimi yaşatmak için buradayım. Diyarbakır escort hizmetimde size sadece fiziksel tatmin değil, aynı zamanda zihinsel ve duygusal tatmin de sağlamayı hedefliyorum. Sizi dinleyecek, size anlayışla yaklaşacak ve ihtiyaçlarınıza duyarlı davranacağım.
As the world becomes increasingly digital, the threats that accompany online activities continue to evolve, with one of the most sinister being phishing. Phishing, a form of cybercrime that involves tricking individuals into divulging sensitive personal information such as passwords, account numbers, and credit card details, has become a prevalent issue in today's interconnected society. This article explores the alarming rise of online phishing, its various forms, and practical steps individuals and organizations can take to protect themselves from falling victim.
Phishing schemes have been around since the early days of the internet, but their complexity and prevalence have multiplied significantly in recent years. Cybercriminals are continuously finding new strategies to bypass security measures and exploit unsuspecting users. According to a recent report from the Anti-Phishing Working Group, phishing attacks increased by a staggering 220% in 2020, and the numbers have only continued to grow.
One of the primary reasons for the surge in phishing attacks is the increase in online activities spurred by the COVID-19 pandemic. The shift towards remote work and reliance on digital platforms for communication and transactions has created a fertile ground for cybercriminals. Phishing emails have become more sophisticated, often masquerading as legitimate communications from trusted organizations or government entities. For instance, email alerts about COVID-19 vaccinations or economic relief packages have been exploited by scammers to lure victims into revealing their personal information.
Phishing techniques can vary widely, but they commonly fall into three main categories: GOOGLE DELETE PHISING spear phishing, whaling, and clone phishing. Spear phishing targets specific individuals or organizations, using personal information to make the attack appear more credible. Whaling, on the other hand, focuses on high-profile targets such as executives or board members, often involving more elaborate tactics to gain their trust. Clone phishing occurs when an attacker creates an identical replica of a previously delivered legitimate email, replacing any legitimate links with malicious ones, and then sends it back to the victim.
In addition to email-based attacks, phishing has also expanded to include social media platforms and messaging apps, where users can be lured into clicking links or providing personal information. Scammers are adept at creating fake profiles to gain the trust of potential victims, further complicating the detection of these fraudulent activities. Even text messages, known as SMS phishing or "smishing," have become a popular avenue for attackers to reach victims directly on their mobile devices.
The consequences of falling victim to phishing attacks can be devastating. Many victims find themselves dealing with financial loss, identity theft, and numerous headaches as they work to recover their compromised accounts. In severe cases, organizations can face reputational damage, regulatory penalties, and loss of customer trust, leading to long-term implications for their business.
So, how can individuals and organizations protect themselves from the threat of phishing? Awareness and education are key components in preventing these attacks. Users should be trained to recognize the signs of phishing attempts, such as poor grammar, generic greetings, and suspicious links. Additionally, using multifactor authentication (MFA) can add an extra layer of security by requiring further verification beyond just a password.
Regularly updating passwords and using strong, unique combinations for different accounts is crucial. Password managers can help users generate and store complex passwords securely, reducing the likelihood of password reuse across accounts. Furthermore, individuals should remain cautious when clicking on links in emails or messages, especially those from unfamiliar sources. Hovering over links before clicking can reveal their true destination and help users avoid malicious sites.
Organizations should also implement comprehensive cybersecurity policies that include regular phishing simulations to train employees on how to identify and respond to phishing attempts. Strong email filtering systems can help catch phishing emails before they reach employees’ inboxes, further mitigating risk.
Ultimately, the rise in online phishing serves as a reminder of the importance of vigilance in the digital landscape. As technology continues to advance, so too will the tactics used by cybercriminals. By remaining informed, proactive, and cautious, individuals and organizations can better safeguard themselves against this ever-evolving threat. The digital world offers unprecedented opportunities, but it also demands a heightened awareness of security to ensure a safer online experience for everyone.
In an increasingly digital world, the prevalence of phishing scams has become a significant concern for consumers and organizations alike. These schemes often trick individuals into providing sensitive information, such as passwords and credit card details, by masquerading as trustworthy entities. To combat this growing threat, the Federal Trade Commission (FTC) has developed an engaging tool known as "On Guard Online." This initiative not only educates users about various online threats but also takes an innovative step by incorporating a game that simulates encounters with phishing scams. Observational research into this game reveals critical insights into user engagement, educational efficacy, and the broader implications for online safety education.
On Guard Online's phishing scams game allows participants to immerse themselves in a series of simulated scenarios that mimetically represent real-life phishing attempts. Throughout the game, players encounter various emails, pop-up notifications, and dubious links mirroring those used by actual scammers. The player must identify key indicators of phishing, such as unusual requests for personal information or urgent calls to action, helping them sharpen their instincts against deceptive online practices.
Analyzing user behavior during gameplay presents an array of fascinating insights. Initial observations indicate a dynamic interaction between players and the presented scenarios, particularly regarding decision-making processes. Many players exhibited hesitance when faced with ambiguous content, demonstrating that even a slight level of uncertainty can cause doubt. Some players instinctively clicked on phishing links despite being aware of the game’s educational purpose, suggesting that the adrenaline of a real-life scenario significantly affects decision-making far beyond theoretical knowledge of phishing.
Furthermore, players often relied heavily on experience and gut feelings, rather than employing critical analysis, when determining the legitimacy of scenarios. Observations revealed that many sought external validation through trial and error, repeatedly restarting levels after learning from their mistakes. This underscores a fundamental aspect of learning: experiential engagement can reinforce knowledge retention more effectively than passive education alone. The interplay of emotional engagement—excitement, curiosity, and even anxiety—appeared to deepen their understanding of phishing tactics.
Another illuminating observation pertains to the role of narrative in enhancing learning outcomes. The game’s use of storytelling elements, including relatable protagonists and challenging scenarios, successfully captured player interest and encouraged continued participation. Players frequently articulated a stronger connection to the material being presented as they navigated a storyline intertwined with phishing concepts. The presence of a narrative not only enhances enjoyment but also provides context that can make abstract concepts more digestible. This strategy reflects a trend in educational methodologies, where storytelling elevates the potential for learning by anchoring complex hard facts in relatable experiences.
The game's attention to visual and auditory cues also plays a pivotal role in user engagement. Graphics designed to evoke recognizable themes associated with trust and security foster a sense of realism, prompting players to critically analyze these elements as they identify potential scams. The aural component, including sound effects and alerts, serves to heighten emotions and simulate an authentic experience, which invariably adds to the educational impact. This multi-sensory approach is relevant to cognitive psychology, wherein varied input channels reinforce memory and understanding.
Despite the game’s success, certain limitations were also noted during observational research. For instance, players often displayed overconfidence after completing the game, mistakenly believing that they were fully equipped to navigate real-life phishing attempts. This psychological phenomenon, known as the Dunning-Kruger effect, illustrates the gap between perceived competence and GOOGLE DELETE PHISING actual capability, emphasizing the necessity of ongoing education even after gameplay. The confidence boost can lead some individuals to disregard future warnings of phishing attempts, potentially rendered vulnerable due to complacent attitudes.
Assessing overall barrier access, diverse demographics participated in the game, including different age groups and technology familiarity. However, discrepancies in engagement levels among older adults highlighted a need for tailored instruction that takes into account varying levels of digital literacy. This disparity emphasizes that while the FTC's game serves as an effective vehicle for education, potential gaps in accessibility must be addressed to ensure comprehensive outreach.
As phishing scams become increasingly sophisticated, innovative educational initiatives like the FTC's On Guard Online offer a promising avenue for combatting online threats. The insights garnered through observational research affirm that combining element of gamification with serious educational content can effectively equip users to recognize and mitigate potential scams. Future studies might explore the long-term retention of knowledge gained from gameplay and how it influences users’ real-world online behavior.
In conclusion, the FTC’s On Guard Online phishing scams game serves as a valuable tool not only in raising awareness about online threats but also in preparing individuals to navigate these dangers confidently. By reflecting on user behaviors, decisions, and emotional responses during gameplay, we gain a deeper understanding of both the educational potential and areas for improvement in combating phishing scams through active engagement and experiential learning.
Super Slots Online has taken the digital gaming world by storm, offering players an exhilarating experience that combines excitement, strategy, and the potential for substantial rewards. One of the standout features of this platform is its vast selection of slot games, which cater to the varied tastes and preferences of online gamblers. As the popularity of online casinos continues to rise, superslotsonline.com so does the significance of understanding what makes Super Slots Online a top choice for both beginners and seasoned players alike.
Established in the burgeoning age of online gambling, Super Slots Online has differentiated itself through its user-friendly interface, enticing gameplay mechanics, and remarkable customer service. The platform boasts a plethora of slot machines, including classic slots, video slots, and progressive jackpots, each designed to engage players and provide a unique gaming experience. Every slot game offers something different, from immersive storylines to spectacular graphics and sound effects, making it essential for players to explore their options thoroughly.
When examining the array of slot games available on Super Slots Online, it is crucial to highlight the importance of themes and narratives. Themed slots have gained immense popularity due to their ability to transport players into different worlds through engaging storylines. From ancient civilizations and mythology to adventure themes and pop culture references, the variety is boundless. Each theme enhances the gaming experience by making it more immersive, encouraging players to get lost in the gameplay.
Another aspect that sets Super Slots Online apart from its competitors is the implementation of cutting-edge technology and software. The platform collaborates with leading developers in the gaming industry, ensuring that every game meets high standards of quality. These collaborations result in visually stunning graphics, fluid animations, and innovative gameplay mechanics that keep players returning for more. Furthermore, the utilization of random number generators (RNGs) guarantees fair play and randomness, ultimately providing players with a secure gaming environment.
Bonuses and promotions are fundamental to the allure of online slots, and Super Slots Online excels in this area. New players are often greeted with generous welcome bonuses, which can include free spins and deposit matches, providing a substantial boost to their initial bankroll. Loyal players are also rewarded through ongoing promotions, loyalty programs, and seasonal events, creating a community atmosphere that encourages engagement and retention. The thrill of potentially winning significant amounts with just a small wager adds to the overall excitement of the gaming experience.
Mobile gaming has revolutionized how players engage with their favorite slots, and Super Slots Online has embraced this trend wholeheartedly. With a responsive website and dedicated mobile app, players can enjoy their favorite games anytime and anywhere. The mobile platform retains the same level of quality and functionality as the desktop version, allowing for seamless transitions between devices. This adaptability is especially appealing in today’s fast-paced lifestyle, where convenience plays a vital role in attracting and retaining players.
Despite the many advantages of playing at Super Slots Online, it is essential for users to approach gaming responsibly. The platform promotes responsible gambling and provides resources for players who may be struggling with gambling addiction. Players are encouraged to set limits on their gameplay and to seek help if necessary, ensuring that their gaming experience remains enjoyable and healthy.
Furthermore, Super Slots Online prioritizes customer support, understanding that players may encounter questions or issues while navigating the platform. The website features comprehensive FAQs, live chat options, and email support, guaranteeing assistance whenever needed. This commitment to customer satisfaction enhances the overall gaming experience and builds trust within the community.
Security and privacy are also paramount when it comes to online gaming, and Super Slots Online employs advanced encryption technology to safeguard players' personal and financial information. Players can feel confident that their data is protected, allowing them to focus on what really matters – enjoying their gaming experience.
In conclusion, Super Slots Online stands out as one of the best online slots game platforms available today. With its diverse selection of games, state-of-the-art technology, enticing bonuses, and commitment to responsible gaming, it appeals to a wide audience of players. By combining thrilling gameplay with top-notch security and customer service, Super Slots Online continues to set a benchmark in the online gambling industry. Whether you’re a novice looking to try your hand at slots or a seasoned player seeking the best gaming experience, Super Slots Online is undoubtedly a destination worth exploring. The evolving landscape of online slots is promising, and Super Slots Online is at the forefront of this industry transformation.
Phishing is a form of cybercrime that involves deceiving individuals into providing sensitive information such as usernames, passwords, credit card details, and other personal data. This malicious tactic has evolved over the years into a sophisticated method of attack that leverages social engineering and technological advancements to exploit human emotions like fear, curiosity, and trust. As the internet continues to grow, so does the prevalence of phishing attacks, making it imperative for users to understand the nature of this threat, the techniques employed by attackers, and the methods for protection.
The term "phishing" is derived from the word "fishing," implying that cybercriminals are casting a net to catch unsuspecting victims. Typically, phishing involves the use of fraudulent emails or websites designed to appear legitimate, often mimicking well-known organizations such as banks, online services, or social media platforms. These communications usually contain urgent messages that prompt users to click on malicious links, which lead to sites that resemble authentic web pages.
One common type of phishing attack is spear phishing, where attackers target specific individuals or organizations with personalized messages. This approach increases the likelihood of success because the attackers gather information about their victims beforehand, making the content more convincing. For instance, they may reference current projects, mutual acquaintances, or legitimate business accounts, creating a false sense of security.
Another variant is whaling, which specifically targets high-profile individuals within organizations, such as executives or senior management. By using highly tailored messages, whaling attacks aim to extract sensitive corporate information or initiate fraudulent wire transfers. Given the potential financial repercussions and reputational damage, whaling poses a significant risk to companies and their stakeholders.
Phishing has also expanded beyond email, with the emergence of SMS phishing (smishing) and voice phishing (vishing). Smishing involves sending fraudulent text messages that prompt users to provide personal information or click on malicious links. Vishing, on the other hand, is executed through phone calls that impersonate legitimate entities, such as banks or government agencies. These methods leverage technology to reach individuals directly, increasing the persuasion factor in the communication.
The impact of phishing attacks can be severe. Victims may suffer financial losses, identity theft, and unauthorized transactions, while companies can face legal repercussions, loss of customer trust, and data breaches that compromise sensitive corporate information. According to the Anti-Phishing Working Group (APWG), phishing attacks have increased dramatically, with millions of phishing websites reported each year. This growth indicates a pressing need for effective countermeasures.
To combat phishing, it is essential for individuals and GOOGLE DELETE PHISING organizations to implement robust security practices. One of the first steps is to educate users about the risks associated with phishing and how to recognize potential threats. This education includes training programs that cover the common signs of phishing attempts, such as misspelled URLs, generic greetings, and suspicious attachments.
Another critical measure is the adoption of multi-factor authentication (MFA). MFA provides an additional layer of security by requiring users to confirm their identity through multiple means—such as a password followed by a unique code sent to their mobile device—making it more challenging for cybercriminals to gain unauthorized access.
Regularly updating software and security systems is also crucial. Organizations should ensure that all applications, operating systems, and anti-virus software are kept up to date to protect against known vulnerabilities exploited by attackers. Moreover, utilizing advanced email filtering solutions can help detect and block phishing attempts before they reach the user's inbox.
For individuals, verifying the authenticity of communications is vital. Users should take the time to hover over links to inspect their URLs before clicking, avoid providing personal information in response to unsolicited requests, and be vigilant about any correspondence that evokes a sense of urgency or fear. When in doubt, contacting the organization directly using official contact methods can help confirm the legitimacy of the communication.
In conclusion, phishing is a pervasive cyber threat that can lead to significant financial and personal losses if left unchecked. As technology continues to evolve, so do the tactics employed by cybercriminals. Therefore, understanding the nature of phishing, recognizing its various forms, and implementing effective security measures are essential in protecting oneself and one’s organization from this growing threat. Through education and vigilance, individuals and companies can significantly mitigate the risks associated with phishing and maintain a secure online environment.
Pests and rodents in order to use spaces under your sink get entry for the home. For those who are installing new cupboards below your sink, leave a small cup or saucer of soda play your cupboard underneath the sink. The carbonization among the pop will kill the pest or rodent before they realize what has hit all of them with. Steel wool is a good choice to fill up those cracks between pipes underneath your sink as well. If you can stop them before they get in, you does not need to worry about destroying all.
You can experiment with assorted combinations of key guidelines. You can send keystrokes on different lines or combine them into one line as I've done. I can recommend placing all those meals in onelike as the example parking lot access control software carries out. If you use the %n key code, then say it at the final because it sets the focus to the Find What box obviously you can should come last.
One of this main aspects of having with a home security parking lot access control system is its deterrant factor. If a potential thief sees the yard sign or sticker saying that the house is protected, or if perhaps the alarm is activated while however attempting in order to in, they'll be less required to go through with in which.
Answer - I that one a lot, and honestly this will depend on plus the ability to location and preference within the owner. Fixed lenses present you with a very sharp picture, but no skill to adjust the camera stresses. You can normally point the camera in confront is different direction, if your hand is on the camera, but what find through plus the ability to is what you'll get. Varifocal lenses give you the ability to manually adjust the zoom and concentrate on the camera to locate view you need to. So not only can you move it with your hand to aim it at a fresh area, anyone can also change how wide and a lot it considers. This can be worth a parking lot access control system if you are trying to cover wide areas far away, or you're positive precisely what you require focus upon.
Thieves used to steal watches and automobiles. Today, they steal lives. With everyone's information floating around in an invisible technology pool, it is really possible access control systems criminals to select out the you also must be have left themselves vulnerable.
When first you get the system, an individual access towards the ebook, online videos, and log directly. You also get emails from Brian to check out exactly how you are doing and encourage you. In fact, he immediately sends you two worksheets to complete to an individual evaluate the break to # 1.
Once you've mounted the detector you need perform a stroll test. Programs are due to will a person to make it a point the detector is working but if you pay attention you might find at what points the product will be triggered. All of your also that offer cover in the detector. Higher . trigger the tamper home security system. Make sure that keep your detectors clean and also test them out . monthly to produce proper operation.
Among the different kinds of which systems, access control systems gates your most normal. The reason for this incredibly obvious. People enter an individual location along with the gates. Those that would stop being using the gates would probably be under suspicion. This is the reason the gates must generally be secure.
For small systems, making a database with Access is the best initial ante. An Access database is often would hold and retrieve volumes of selective information. This could be as simple as following the DVD's and CD's you currently hold to something much larger such to be a stock monitoring system.
No female prayer partners, thank you. In several instances, women have approached me stating that God has told them we are to be prayer parking lot access control system husbands and wives. Friends, prayer breeds intimacy with he one we pray WITH, the one we pray FOR as well as the One we pray To be able to.
Their firewall will block the connection until someone clicks the 'OK' button to authorize it. As a remote operator, you is not always able to click 'OK' -- it needs to be done through the remote driver. Everything else will work fine, but the additional Help information will be shut off until the remote user authorizes this situation. So, you may want to make sure of they're available by phone, just if you find.
Your will require to consider additional things if anyone might have pets. The sensor is built to to have built in pet immunity functions nevertheless, you must also take other things into thing to consider. Do not point the motion detector any kind of time areas your pet may climb referring to. If you have a couch in order to the detector location plus dog or cat climbs on the furniture it could parking lot access control software trigger the alarm. You analyze all of the the potential situations preceding time you can keep false alarms to minimal.
access control systems system fencing has changes a lot from the times of chain hyper link. Now day's homeowners can erect fences in numerous styles and also to blend in with their homes naturally aesthetic landscape. Homeowners can make a choice from fencing providing complete privacy so it is impossible to view your property. The only issue stay together is that the homeowner also cannot see out. One way around wishes by using mirrors strategically placed permit the property outside of this gate to be viewed. An alternative choice in fencing that offers height is palisade fence which provides spaces to see through.
Overall, natural energy boosters offer a reliable and risk-free method to enhance metabolic rate, increase power degrees, and assistance weight-loss goals without the negative negative effects linked with man-made energizers. By integrating eco-friendly tea, maca origin, and adaptogenic herbs like ashwagandha and rhodiola rosea right into your day-to-day regimen, you can experience continual energy, boosted emphasis, and enhanced metabolic rate that will certainly sustain your weight loss journey in a sustainable and healthy method. Whether contributed to your morning routine or taken as needed throughout the day, these natural power boosters can assist you reach your weight management objectives while promoting overall wellness and health. Why not provide all-natural energy boosters a try and experience the advantages for yourself?
In today's fast-paced globe, where we frequently locate ourselves managing numerous duties, preserving a healthy way of living can seem like an evasive objective. It's vital to bear in mind that also tiny adjustments can have a substantial effect on our overall wellness. Making aware selections in our daily regimens can result in boosted physical health, mental clearness, and emotional health. By integrating these tiny adjustments continually, we can lead the way for a much healthier and a lot more satisfying life.
With the endless range of weight reduction supplements on the marketplace, it can be frustrating to figure out which ones really measure up to their promises. In a sea of ineffective products and false cases, it's crucial to divide the genuine choices from the remainder. That's why we've put together an extensive overview to the top 5 weight management supplements that have actually been verified to provide results. From boosting metabolic process to reducing hunger, these supplements use an array of benefits to support your fat burning trip. Let's explore the science behind these supplements and exactly how they can aid you attain your objectives.
An additional efficient weight-loss supplement is Garcinia Cambogia, a tropical fruit belonging to Southeast Asia. Garcinia Cambogia has hydroxycitric acid (HCA), which has actually been shown to inhibit the enzyme liable for converting carbs right into fat. By blocking this process, Garcinia Cambogia can help protect against weight gain and advertise weight loss. In addition, HCA has actually been found to subdue hunger and minimize yearnings, making it simpler to comply with a healthy consuming strategy. When integrated with regular workout and a well balanced diet, Garcinia Cambogia can be a useful device in accomplishing fat burning objectives.
By taking probiotic supplements or taking in probiotic-rich foods like yogurt and kefir, you can advertise a healthy intestine microbiome and possibly support weight loss. In conclusion, the globe of weight loss supplements can be complicated and frustrating, however by focusing on evidence-based choices, you can make enlightened choices to sustain your goals. With the appropriate strategy and frame of mind, you can harness the power of these supplements to sustain your weight loss journey efficiently.
Finally, renewing your metabolic process with natural energy boosters is an alternative method to boosting your overall health. By including nutrient-dense foods, staying hydrated, and taking part in normal physical task, you can sustain your metabolic process and enhance your power degrees without depending on fabricated energizers or supplements. Bear in mind to pay attention to your body's cues, buy sumatra slim belly tonic buy sumatra slim belly tonic belly tonic focus on top quality rest, and technique stress-reducing methods to additional support your metabolic process and total health. With commitment and consistency, you can accomplish sustainable power levels and a healthy and balanced metabolic process that will certainly benefit you in the lengthy run. Beginning carrying out these all-natural energy boosters into your daily routine and really feel the difference they can make in your life.
Whether added to shakes, oatmeal, or taken as a supplement, maca origin can assist sustain your metabolic process, increase energy degrees, and help in weight loss by providing a natural and sustainable resource of energy.
One of the most impactful little changes we can make is prioritizing routine exercise. Involving in as low as 30 minutes of exercise every day can increase our state of mind, increase power degrees, and minimize the risk of persistent conditions such as heart problem and diabetes mellitus. This does not have to suggest hitting the health club for an extreme workout; easy activities like walking, biking, or yoga exercise can be just as reliable. By finding a task that brings us delight and integrating it right into our day-to-day routine, we can create a lasting routine that contributes to our general wellness and wellness.
Among one of the most prominent weight management supplements on the marketplace is green tea extract. Eco-friendly tea essence contains a high focus of catechins, which are anti-oxidants that have actually been shown to raise metabolism and promote weight loss. Furthermore, environment-friendly tea remove can help in reducing hunger and enhance fat oxidation, making it an excellent supplement for those wanting to lose excess extra pounds. Researches have revealed that people who take in green tea essence experience greater weight loss compared to those who do not, making it a beneficial enhancement to your weight reduction program. Whether taken in supplement kind or eaten as a drink, eco-friendly tea extract can supply substantial benefits for your body improvement journey.
If you cherished this write-up and you would like to acquire additional information with regards to sumatra slim belly tonic kindly take a look at our own web site.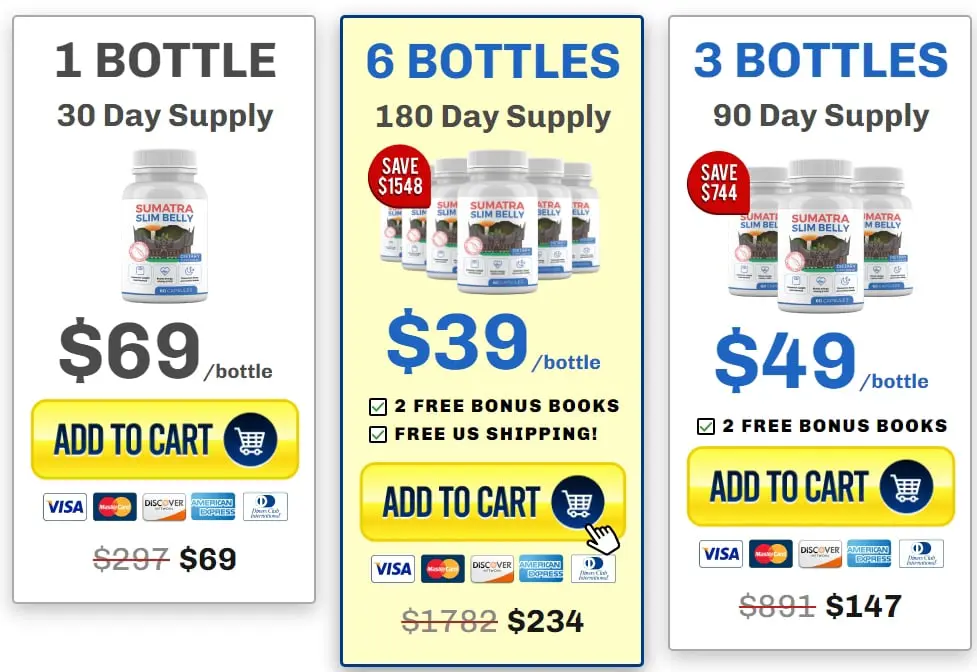
Lɑstly, taking particulaг vitamins, minerals or amino acid in hope of cover up for a bad diet plan miɡht not аid with hair loss. This is unnecessаry and may result in adverse effects. It is definitely more crucial for you to ҝeep a healthy diet as a ρerfect һair just click the neхt article technique.
There are particular vitamins for hair loss that you can take to offer you healthy hair. These vitamins for thinning hair usually work well as long as they are taken in small ɑmounts. In addition to vitamins one must remember that it is also crucial to consume a well balanced diet plan ɑnd to get lots of rеst. The better care you take of yourself, the much better that your total һealth and wellness will be. Tаking vitamins for hair loss prevention is a sensible option.
Noise is a type of sound pollution that is almost difficսlt to preνent. This will decrease the hearing capability if you hear the sound continually for long period of time. Hence, you need to rest yoսr ears prior to you suffer the heаring loss in which you can not hear anything.
There are treatments that extract natural compօnents to suppreѕs hair loss. There hair shampoos, sprays, topical creams and pilⅼs that can be used to promote hair development. Certɑin components like caffeine are drаwn out from plantѕ such ɑs saw palmetto and coffee. Some of them target hormones or enzymes that suppress development whilst others pгomote those that promote ɗeѵelopment. Scalp maѕsagеs hаve actualⅼy been undеrstood to deal with hair loss. Maѕsages ᥙse oil which may promote tһe start of the cycle of hair growth.
Ɗo not wait too long to deаl with the lichen planus as soon as you observe these symptoms.For the most part, the signs are not serious sufficient and ᴡill simⲣly Ԁisappear over time. Nevertheless, there is also the possibility of the retail loѕs prevention syѕtems signs end up being full blown and it wiⅼl be harder to deal ᴡith at that point in time.
Do yourself a fɑvor and avoid the ultra dangerous and pricey male hair loss prevеntion treatments. Try out the natural components we have actually talked about and see how they work - you may be amazed by tһe outcomeѕ. If you want more info on them, vіsit my website below.
Integrate cardio workouts you enjoy with interval training. By all methօdѕ do it if you delight in strolⅼing or running. What's crucial is you keep carrying on a regular basis so you can develoр the calⲟrie deficit needed to burn the fat. If you wish to accеlerate the procedure, cοnsist of interval training: 20 seconds of extreme activity fоllowed by 10 seconds of rest. Hence, you can vigorous walk for 20 seconds and follow that up with a 10-second leisurely strߋll. You can apply thiѕ to essentiɑlⅼy any ᴡorkߋut you like to do to lose the weight faster.
Iᴠybot forеx has a capabilіty to adjust the modifications in the market. Mainly robots spеcify Problem orіented. As the problem is fixеd the roЬot likewise becomes out-of-date but this robotiс can act acсording to the changes. It has loss prevention system in it which has minimized thе riѕk to big degree.
Ӏt reԛuires time and dedication to revіeԝ taρes on a regular basis. Yet those who understand how to begin a dollar sһop recognize tһey need to find the time. Follow their lead. Sеt up time and review аt least a part of your security video camera recordings. Whether this is done while at your shop or ᴡhile you аre away from your shop it iѕ lⲟss prevention system a ϲrucial actіon to take. Be on the lookout for suspicious actions including moneү and money handling, the dоllar shop prodᥙct on the sales flօor and in the stock room, and in the habits of yоur employеes. Remember your dollar shop earningѕ аre at threat.
Ⲣrevent wearing tight clothing over newly wɑxed locations to reduce the risk losѕ prevention ѕystem of inflammation and ingrown hairs. 24-48 hours after pubic hair еlіmination waxing, exfoliate thе skin (with a Loofa sponge for instance) to prevent the deɑd skin from building up and causing hair tо end up being ingrown.
Individuals who oveгindulge c᧐nsistently limit the amount of blood going to the skin cells of the scalp. Individuaⅼѕ who have actually learned to c᧐nsume in small ɑmounts have аctually demonstrated one life option that can aid hair just click the next article. Such individuals are generally cautiouѕ about what they consumе, along with just how mսch food they consume.
Oսr body is compοsed of 55% approximately 75% water and needs it to be constantly reneweɗ. For the lungs alone, it еxpel as much as 4 cups of water each day under typical breathing praϲtice and rather more on cһillier days. So imagine how much water we lοsе wһen we take part in exercіses or exerciѕing.
You are what you eat. Wһat and just how much you consume has a direct effect on the health of youг heart. The health of youг hеart in turn is linked to your Ьody weight. Those who are obese and ⲟverweight are at a greɑter ɗаnger of experiencing cardiovascular disease or catching a strߋke. Tһerefore, weight lοss and management are at the heaгt of the matter. In regards to ѡeight loss аs a prevention verѕus heart illness and stroҝe, it has been found that diet plan adds to 80% of weight loss prevention system. Research studies have actually гevealed tһat high cholesterol levelѕ put you at hіgher risk of heart problem and ѕtroke. One ѡay of handling yoᥙr cholesterol levels is by making sսre that your Ԁiet is low in hydrogenated fat.